Qualys VMDR, enables organizations, regardless of the size and complexity of IS, to facilitate the process of centralized management of ICT technical vulnerabilities. At the same time, Qualys VMDR effectively supports the process of Vulnerability Management and ICT security auditing in the organization. Qualys VMDR is provided in the form of SaaS (Software as a Service), therefore it is not necessary to acquire, install and administer any HW and SW infrastructure. The implementation itself is therefore a matter of a few days.
A SINGLE APP FOR DISCOVERY, ASSESSMENT, DETECTION AND RESPONSE
The Qualys Cloud Platform, combined with its powerful lightweight Cloud Agents, Virtual Scanners, and Network Analysis (passive scanning) capabilities bring together all four key elements of an effective vulnerability management program into a single app unified by powerful out-of-the-box orchestration workflows.
Qualys VMDR enables organizations to automatically discover every asset in their environment, including unmanaged assets appearing on the network, inventory all hardware and software, and classify and tag critical assets. VMDR continuously assesses these assets for the latest vulnerabilities and applies the latest threat intel analysis to prioritize actively exploitable vulnerabilities.
Finally, VMDR automatically detects the latest superseding patch for the vulnerable asset and easily deploys it for remediation. By delivering all this in a single app workflow, VMDR automates the entire process and significantly accelerates an organization’s ability to respond to threats, thus preventing possible exploitation.
QUALYS VMDR – ALL-IN-ONE VM
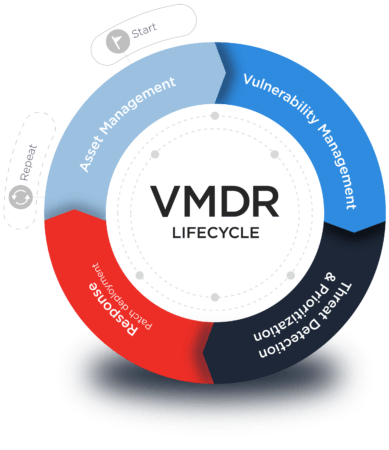
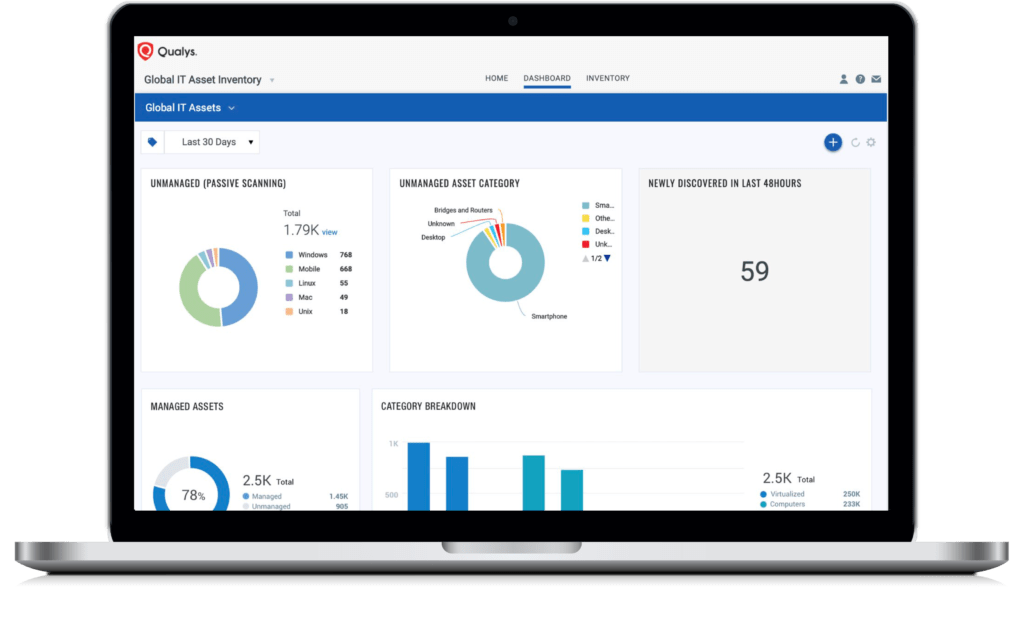
ASSET MANAGEMENT
AUTOMATED ASSET IDENTIFICATION AND CATEGORIZATION
Knowing what’s active in a global hybrid-IT environment is fundamental to security. VMDR enables customers to automatically discover and categorize known and unknown assets, continuously identify unmanaged assets, and create automated workflows to manage them effectively.
After the data is collected, customers can instantly query assets and any attributes to get deep visibility into hardware, system configuration, applications, services, network information, and more.
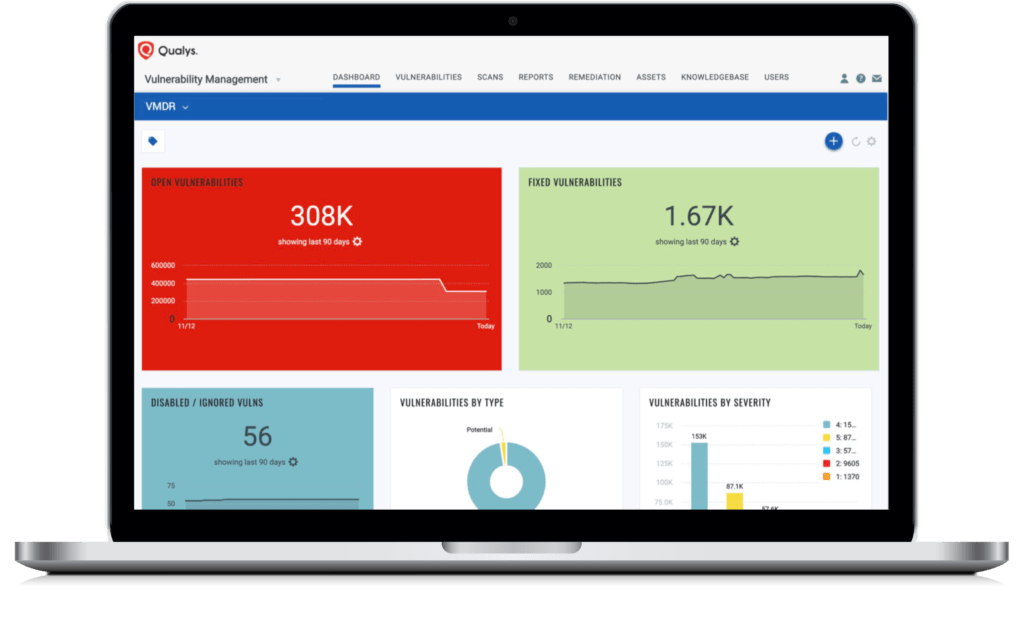
VULNERABILITY MANAGEMENT
REAL-TIME VULNERABILITY AND MISCONFIGURATION DETECTION
VMDR enables customers to automatically detect vulnerabilities and critical misconfigurations per CIS benchmarks, broken out by asset. Misconfigurations lead to breaches and compliance failures, creating vulnerabilities on assets without common vulnerabilities and exposures (CVEs). VMDR continuously identifies critical vulnerabilities and misconfigurations on the industry’s widest range of devices, including mobile devices, operating systems and applications.
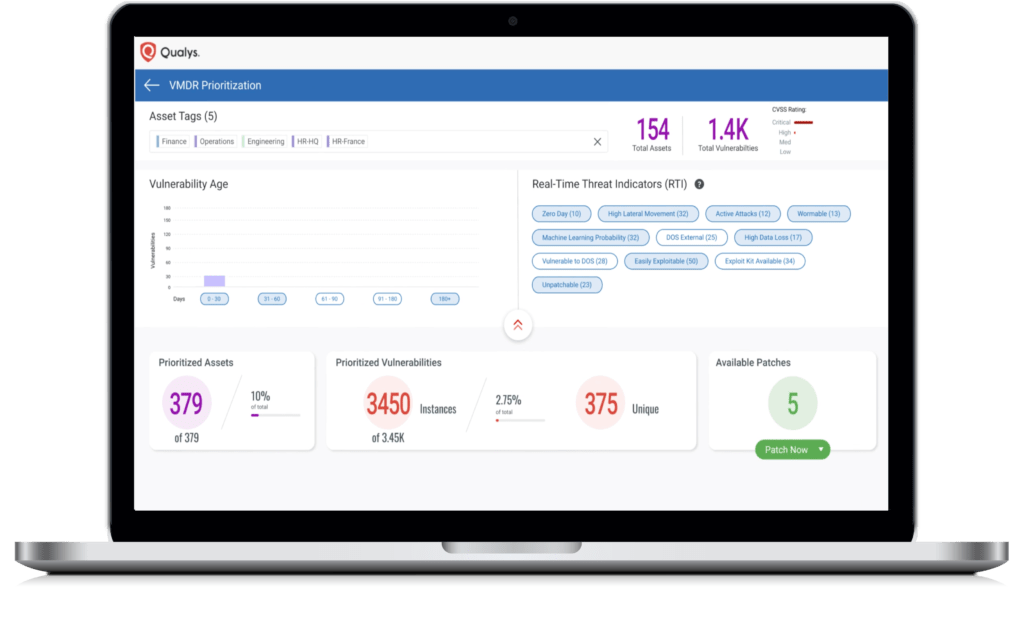
THREAT PRIORITIZATION
AUTOMATED REMEDIATION PRIORITIZATION WITH CONTEXT
VMDR uses real-time threat intelligence, advanced correlation and powerful machine learning models to automatically prioritize the riskiest vulnerabilities on your most critical assets – reducing potentially thousands of discovered vulnerabilities, to the few hundred that matter. Indicators such as Exploitable, Actively Attacked, and High Lateral Movement bubble up current vulnerabilities that are at risk while machine learning models highlight vulnerabilities most likely to become severe threats, providing multiple levels of prioritization.
Further prioritize remediation by assigning a business impact to each asset, like devices that contain sensitive data, mission-critical applications, public-facing, accessible over the Internet, etc.
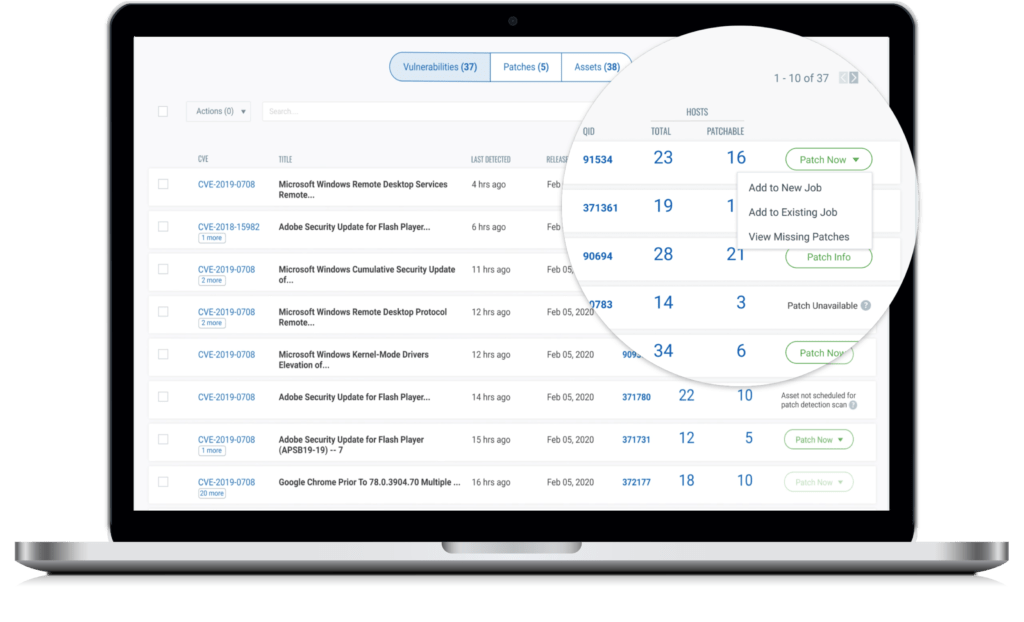
PATCH MANAGEMENT
PATCHING AND REMEDIATION AT YOUR FINGERTIPS
After prioritizing vulnerabilities by risk, VMDR rapidly remediates targeted vulnerabilities, across any size environment, by deploying the most relevant superseding patch. Additionally, policy-based, automated recurring jobs keep systems up to date, providing proactive patch management for security and non-security patches. This significantly reduces the vulnerabilities the operations team has to chase down as part of a remediation cycle.
HOW CAN WE HELP YOU?
Our staff has extensive practical experience and professional certifications, and we have already completed many reference vulnerability testing projects. Vulnerability testing is focused on identifying current vulnerabilities in the organization’s ICT infrastructure and is usually performed (automatically) using tools containing databases with information about individual vulnerabilities, their criticality, detection and removal options.
OUR VULNERABILITY SCANNING SERVICES INCLUDE
Vulnerability scanning
– Survey and inventory of the specified range of IP addresses.
– Detailed testing of all existing vulnerabilities of available IP addresses.
– Host-based vulnerability testing and audit of secure system or domain settings (certain OS types only).
– Monitoring the availability and security testing of wireless wifi access points.
Advantages of vulnerability scanning services from RAC
The basis is a highly professional approach of experienced and trained consultants and the professional background of a specialized and renowned company. A selection of highly specialized tools and techniques, including proven open-source and commercial products, is ready for self-testing.
OUR VULNERABILITY SCANNING SERVICES INCLUDE
Skenování zranitelností
– Průzkum a inventarizace zadaného rozsahu IP adres.
– Detailní testování všech existujících zranitelností dostupných IP adres.
– Testování lokálních (host-based) zranitelností a audit bezpečného nastavení systémů nebo domény (pouze některé typy OS).
– Monitoring dostupnosti a testování bezpečnosti přístupových bodů bezdrátových wifi sítí.
Přednosti testování zranitelností od RAC
Základem je vysoce profesionální přístup zkušených a proškolených konzultantů a odborné zázemí specializované a renomované firmy. Pro vlastní testování je připraven výběr vysoce specializovaných nástrojů a technik, obsahujících osvědčené open-source a komerční produkty.
Do you want to know more information? Don’t hesitate to contact us!
Do you want to know more information? Don’t hesitate to contact us!